Role in the pipeline
StørmOps provides deployment posture, observability, and governance workflows for models, policies, and schemas, and tracks SLO/SLA targets under load.
Contract: telemetry + configs → posture + controls
Operational inputs transformed into governed posture and controls.
Inputs
Telemetry, SLO targets, and governed configuration bundles.
Processing
Posture evaluation, rollout orchestration, and approvals.
Outputs
Operational posture, control decisions, and sealed audit trails.
Interfaces
- Inputs: telemetry from ingestion, inference, graph, decision, and control modules.
- Outputs: governance decisions, deployment posture states, and audit artefacts.
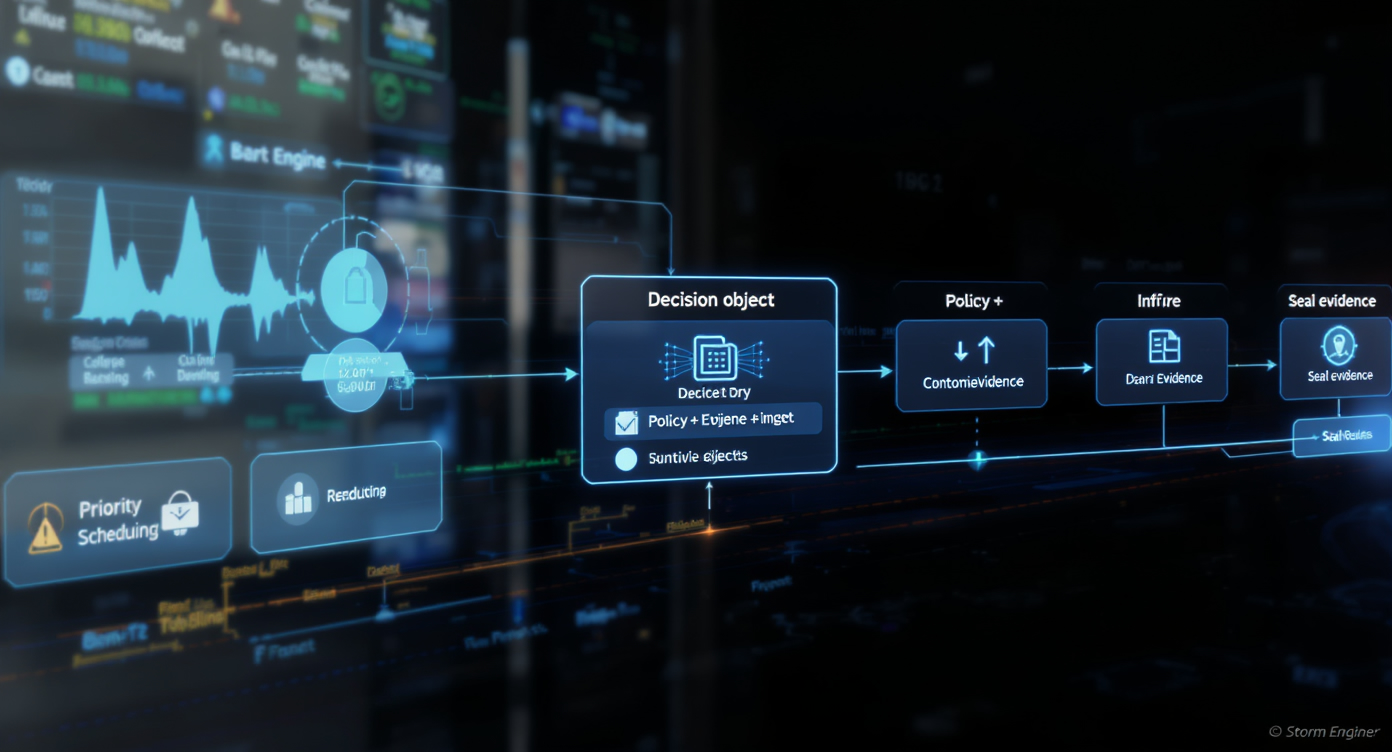
Operational governor for the pipeline.
StørmOps coordinates observability, governance, and safe change.
It frames SLO/SLA targets and monitors adherence.
Changes are staged, approved, and recorded for audit.
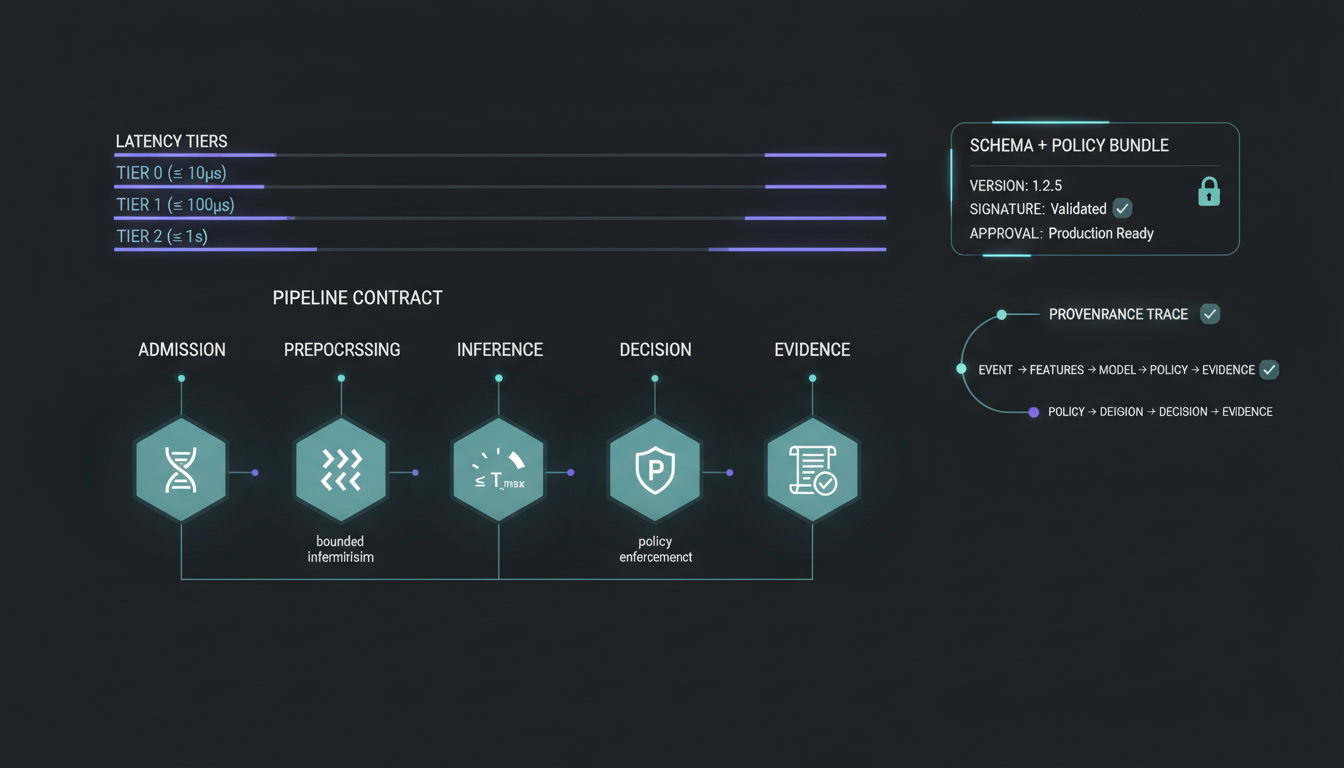
Operational contracts.
- SLO/SLA targets are defined per tier and monitored continuously.
- Governed artifacts require approval and staged rollout.
- Failover and degradation modes are configurable.
- Operator actions are audited and sealed in StørmVault.
- Telemetry is versioned and attributable.
Governed change lifecycle
- Propose: submit model, policy, or schema changes for review.
- Validate/approve: verify signatures, tests, and approvals.
- Deploy with rollback: staged rollout with rollback controls.

Governance controls
- Version pinning for models, policies, and schemas.
- Rollout waves with staged approvals.
- Operator approvals and change windows.
- Audit exports and attestation bundles.
Capabilities
Operational posture, observability, governance workflows, and safe change management.
SLO/SLA posture and telemetry
Tracks SLOs, queue depth, decision latency, evidence sealing health, and error budgets across the pipeline. So what: operators can see when targets drift.
Models, policies, and schemas
Approvals, versioning, and staged rollouts for governed artifacts with sealed audit trails in StørmVault. So what: changes are controlled and reversible.
Failover and safe-mode posture
Configurable failover and degradation modes preserve enforcement-critical paths while deferring non-critical analytics. So what: enforcement stays available under stress.
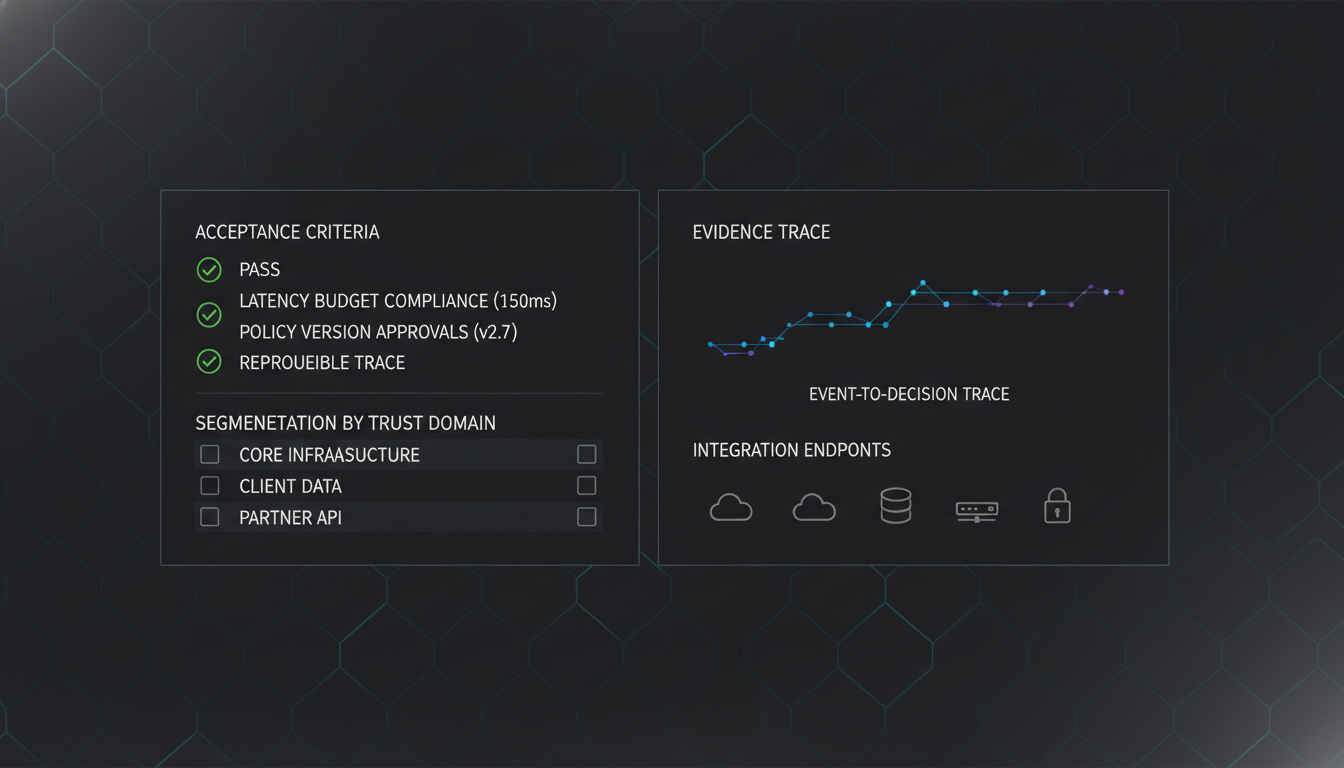
Access, approvals, and audit trails
Role-based access, approval workflows, and immutable audit trails protect the operational control surface. So what: operator actions remain accountable.