Role in the pipeline
StørmControl is the execution layer: it accepts policy-bounded decision objects and performs environment-specific actions across identity, network, and system layers.
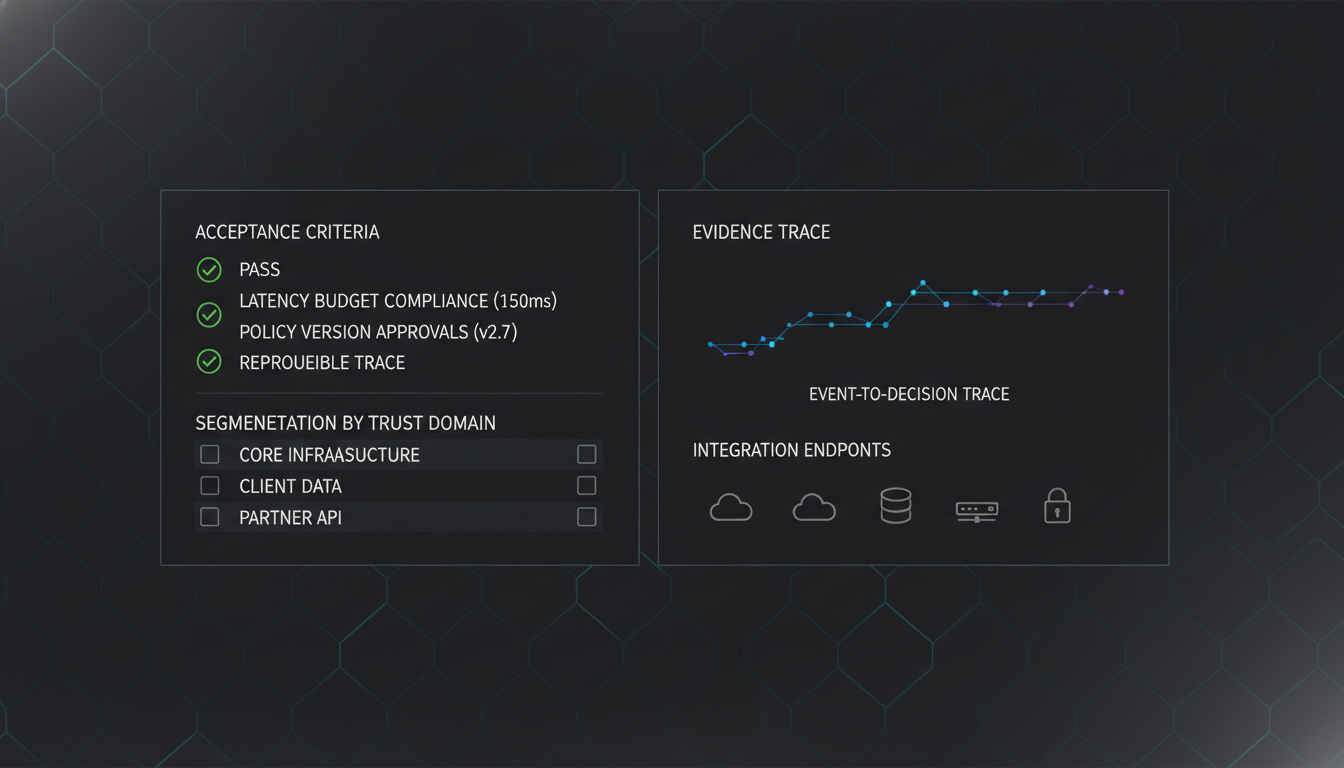
Contract: decision → actions → receipts
Inputs, execution, and sealed acknowledgement records.
Inputs
StørmDecision objects with policy references and action scope.
Processing
Playbook selection with timeouts and acknowledgement tracking.
Outputs
Enforcement receipts sealed to StørmVault with telemetry.
Interfaces
- Inputs: decision object and enforcement plan.
- Outputs: action executions, acknowledgements/timeouts, evidence pointers.
- Integrations: identity, network, endpoint, key/session controls.
- Failure semantics: backpressure, degraded mode, and bounded retries.
The hands of the pipeline.
StørmControl turns decision objects into concrete actions.
It enforces guardrails, approvals, and reversibility constraints under sovereign oversight.
Execution results are recorded as receipts and telemetry.
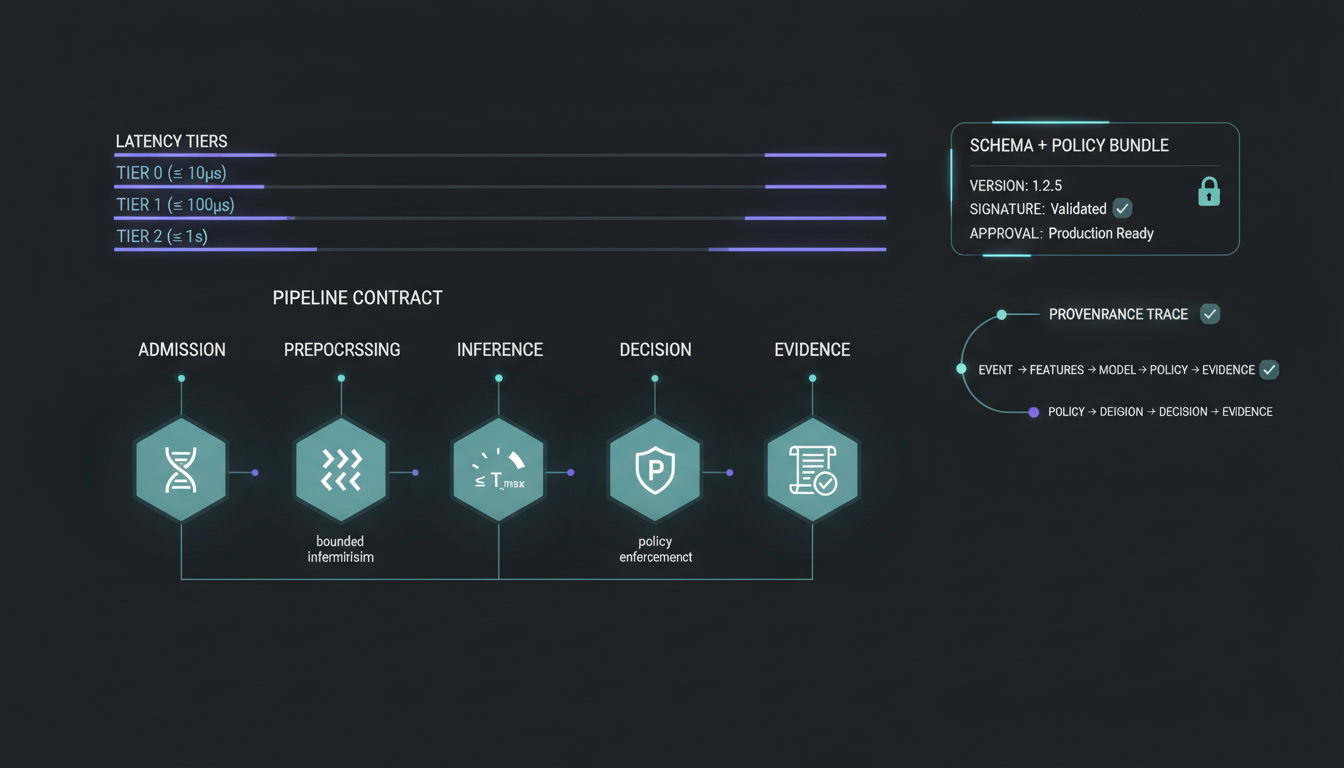
Execution contracts.
- Consumes decision objects with policy clauses and action plans.
- Executes reversible and irreversible actions with explicit labels.
- Timeouts and retries are bounded per action class.
- Receipts and telemetry are sealed in StørmVault.
- Failures are recorded as security events.

Safety constraints
- Rate limits to prevent runaway enforcement loops.
- Allowlists for permitted action types.
- Rollback paths for reversible changes.
- Approvals for high-impact actions.
Capabilities
Inputs, outputs, guarantees, and failure handling.
Decision object + policy constraints
StørmControl consumes:
- Decision objects with action recommendations and policy references.
- Trust context from StørmTrust (session state, artifact verification).
- Integration credentials and environment configuration.
So what: actions are tied to verified inputs and context.

Layered execution targets
- Crypto: key rotation, certificate revocation, session termination.
- Identity: account disablement, privilege reduction, MFA resets.
- Network: segment isolation, flow blocks, firewall updates.
- System: host quarantine, process termination, token revocation.
So what: actions are scoped to explicit layers and controls.
Receipts and execution telemetry
Emits action receipts and acknowledgements to StørmOps, and writes execution telemetry and enforcement outcomes to StørmVault. So what: execution outcomes are traceable.
Timeouts, retries, and reversibility
Actions carry timeouts, retry policy, and reversible/irreversible labels to prevent unsafe loops and maintain stability under load. So what: enforcement remains stable under stress.

Escalation when actions fail
If enforcement cannot be confirmed within bounds, the failure is recorded as a security event and can trigger secondary containment. So what: failures become actionable security events.
Guardrails for controlled execution
- Human approval gates for high-impact actions.
- Dry-run mode for validation and tuning.
- Reversible actions labeled and prioritized.
- Scoped blast radius aligned to StørmGraph outputs.
So what: enforcement stays controlled and reviewable.